Address Resolution Protocol (ARP)
The job of the ARP is essentially to translate 32-bit addresses to 48-bit addresses and vice-versa. This is necessary because in IP Version 4 (IPv4), the most common level of Internet Protocol (IP) in use today, an IP address is 32-bits long, but MAC addresses are 48-bits long.
ARP works between network layers 2 and 3 of the Open Systems Interconnection model (OSI model). The MAC address exists on layer 2 of the OSI model, the network layer, while the IP address exists on layer 3, the data link layer.
ARP can also be used for IP over other LAN technologies, such as token ring, fiber distributed data interface (FDDI) and IP over ATM.
In IPv6, which uses 128-bit addresses, ARP has been replaced by the Neighbor Discovery protocol.
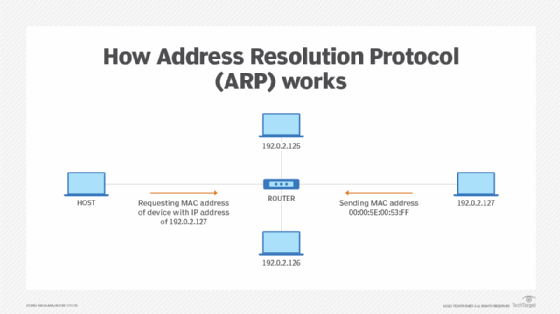
How ARP works
When a new computer joins a LAN, it is assigned a unique IP address to use for identification and communication. When an incoming packet destined for a host machine on a particular LAN arrives at a gateway, the gateway asks the ARP program to find a MAC address that matches the IP address. A table called the ARP cache maintains a record of each IP address and its corresponding MAC address.
All operating systems in an IPv4 Ethernet network keep an ARP cache. Every time a host requests a MAC address in order to send a packet to another host in the LAN, it checks its ARP cache to see if the IP to MAC address translation already exists. If it does, then a new ARP request is unnecessary. If the translation does not already exist, then the request for network addresses is sent and ARP is performed.
ARP broadcasts a request packet to all the machines on the LAN and asks if any of the machines know they are using that particular IP address. When a machine recognizes the IP address as its own, it sends a reply so ARP can update the cache for future reference and proceed with the communication.
Host machines that don’t know their own IP address can use the Reverse ARP (RARP) protocol for discovery.
An ARP cache size is limited and is periodically cleansed of all entries to free up space; in fact, addresses tend to stay in the cache for only a few minutes. Frequent updates allow other devices in the network to see when a physical host changes their requested IP address. In the cleaning process, unused entries are deleted as well as any unsuccessful attempts to communicate with computers that are not currently powered on.
Proxy ARP
Proxy ARP enables a network proxy to answer ARP queries for IP addresses that are outside the network. This allows packets to be successfully transferred from one subnetwork to another.
When an ARP inquiry packet is broadcast, the routing table is examined to find which device on the LAN can reach the destination fastest. This device, which is often a router, becomes a gateway for forwarding packets outside the network to their intended destinations.
ARP spoofing and ARP cache poisoning
Any LAN that uses ARP must be wary of ARP spoofing, also referred to as ARP poison routing or ARP cache poisoning. ARP spoofing is a device attack in which a hacker broadcasts false ARP messages over a LAN in order to link an attacker’s MAC address with the IP address of a legitimate computer or server within the network. Once a link has been established, the target computer can send frames meant for the original destination to the hacker’s computer first as well as any data meant for the legitimate IP address.
ARP spoofing can have serious impacts on enterprises. When used in their simplest form, ARP spoofing attacks can steal sensitive information. However, the attacks can also go beyond this and facilitate other malicious attacks, including:
History and future of ARP
ARP was first proposed and discussed in Request for Comments (RFC) 826, published in November of 1982 by David C. Plummer. The problem of address resolution was immediately evident in the early days of the IP protocol suite, because Ethernet quickly became the preferred LAN technology and Ethernet cables required 48-bit addresses.
In IPv6, network nodes use a protocol called Neighbor Discovery (ND) to acquire configuration information. Neighbor Discovery operates in the Link Layer (Layer 2) of the OSI model and uses Internet Control Message Protocol (ICMP) version 6 to discover neighboring nodes.